Throughout 2020, the ACSC undertook an extensive review of the Essential Eight Maturity Model to ensure that it continues to be relevant in our current cyber threat environments.
This review was based on the ACSC’s experience in producing cyber threat intelligence, responding to cyber security incidents, conducting penetration testing, and assisting organisations to implement the Essential Eight. As part of this review, they sought feedback from across Federal and State/Territory governments and other ACSC network partners.
The reintroduction of Maturity Level Zero.
The redefinition of existing maturity levels based on degrees of adversary tradecraft sophistication and targeting rather than degrees of alignment with the corresponding mitigation strategy.
No longer expecting all organisations to meet Maturity Level Three. Rather, encouraging organisations to assess their threat environment and select the appropriate maturity level.
A strengthened focus on using a risk-based approach rather than a compliance-based approach, as ASD recognise many organisations have legacy systems, carry technical debt or have systems that aren’t based upon secure-by-design principles which inhibits full implementation of our advice.
An increased emphasis on implementing the mitigation strategies as a package due to their complementary nature and focus on various cyber threats. For example, by implementing all Essential Eight mitigation strategies to Maturity Level One before moving onto Maturity Level Two.
Ensuring all technical guidance for each maturity level was robustly contested and guided by lessons learnt from 2019 Essential Eight sprints for Federal Government and major cyber security incidents (such as Copy-Paste Compromises) that the ACSC responded to throughout 2020.
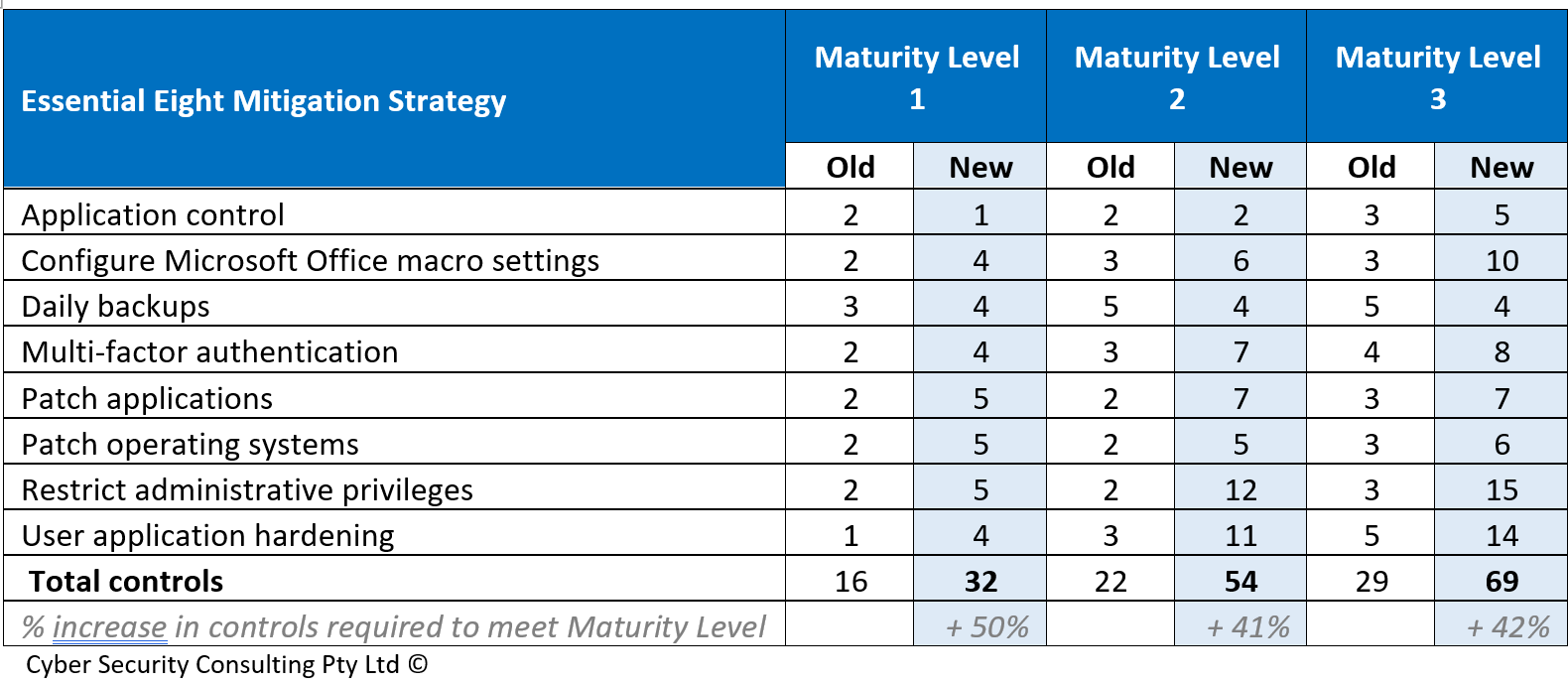
Contrary to its title the Essential Eight has more than eight controls defined within its framework. Essential Eight refers to “Mitigation Strategies”. Each mitigation strategy has one or more controls.
The table below shows the volume of controls required to achieve the old Essential Eight Mitigation Strategy Maturity Levels vs. the revised Essential Eight Mitigation Strategy Maturity Levels.
This maturity level signifies that there are weaknesses in an organisation’s overall cyber security posture. You achieve this level if you don’t implement all the controls in Maturity Level 1. When exploited, weaknesses in your systems could compromise the confidentiality, integrity or availability of information assets or systems.
Controls: Anything less than all of the controls listed under Maturity Level 1.
Suits: Business managing photos of cats or other data assets that do not need to be protected.
What does this level defend against?
Maybe some kids, maybe not?

The focus of this maturity level is to out in place the key controls to combat against adversaries who are looking for any victim rather than a specific victim.
Controls: Read full list of Controls
Suits: ASD state that generally, Maturity Level One may be suitable for small to medium enterprises.
What does this level defend against?
Threat actors who can leverage commodity tradecraft that is widely available in order to gain access to, and likely control of, systems. For example, exploiting a security vulnerability in an internet-facing service which has not been patched, or authenticating to an internet-facing service using credentials that were stolen or guessed.

The focus of this maturity level is enhance controls for companies who have valuable enough data or market presences that makes investment by threat actors in developing tools and deploying more advanced techniques worthwhile.
Controls: Read full list of Controls
Suits: ASD state that generally, Maturity Level Two may be suitable for large enterprises.
What does this level defend against?
Threat actors who are willing to invest more time and money breaching your companies security controls. This includes actively targeting credentials using phishing and employing technical and social engineering techniques to circumvent weak multi-factor authentication. They may target your privileged access users or depending on their intent, also destroy all data (including backups) accessible to an account with special privileges.

The focus of this maturity level is enhance controls for companies who have valuable enough data or market presence where threat actors are a significant concern and are likely to be deploying adaptive techniques.
Controls: Read full list of Controls
Suits: ASD state that generally, Maturity Level Three may be suitable for critical infrastructure providers and other organisations that operate in high threat environments.
What does this level defend against?
Threat actors who may be looking to exploit weaknesses in the existence of older software or inadequate logging and monitoring. These adversaries will likely focus on particular targets, invest in circumventing the particular policy and technical security controls you may have in place and look to evade detection and solidify their presence in your systems for a period of time to achieve their goals. Once a foothold is gained in your system, they may seek to gain privileged credentials or password hashes, move on to other parts of your network, and cover their tracks. Depending on their intent, adversaries may also destroy all data (including backups).
